Code-to-Cloud Security: How we Scan Workloads (and Code) Without Breaking Production
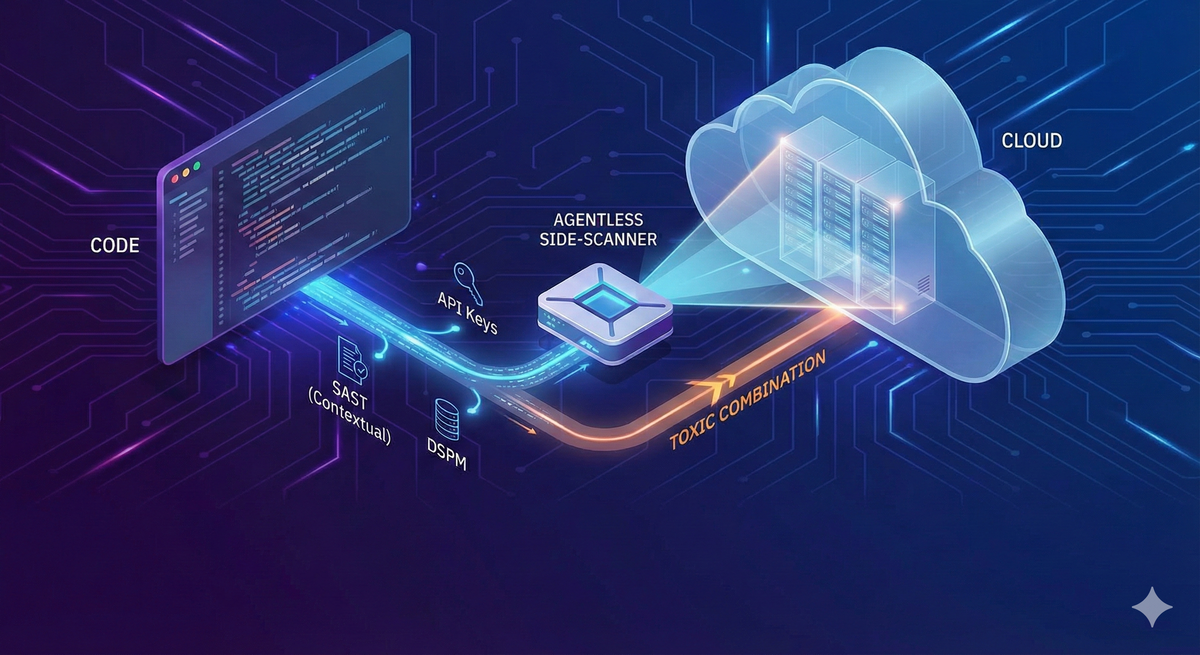
The "Side-Scanning" Revolution (Agentless Security)
The core problem with traditional security is that it tries to run "inside the house." It sits on the server, fighting for resources.
Our approach separates the duties:
- For Scanning (Agentless Side-Scanning): Instead of installing software on the live servers processing our data, our security solution connects to the cloud layer (GCP) via API. It takes a temporary "snapshot" of the server’s disk, analyzes it in a completely isolated environment, and scans that for viruses and vulnerabilities. Once the scan is done, the snapshot is deleted.
- For Real-Time Defense (Sensors): While scanning happens on the side, we use our platform's lightweight Sensors on our clusters. These provide enhanced real-time runtime depth, allowing us to spot active attacks like a hacker trying to execute malicious code in memory and offering forensic-like capabilities to investigate incidents instantly.
Why this matters to us:
- Zero Performance Impact: We can scan a server running a massive, complex tax calculation at peak load, and the server won’t even know we are there.
- 100% Visibility: We don't need to "install" anything. If a developer spins up a new server at 2:00 AM, the platform detects it immediately, there are no blind spots.
The "Contextual" SAST: Fixing the Noise
For years, SAST (Static Application Security Testing) was the bane of an engineering team's existence. Traditional SAST tools scan source code and flag everything that looks remotely wrong. A team could get 5,000 alerts, and 4,990 of them would be false alarms.
Our Cloud Security Platform changes this by adding Runtime Context to our SAST scanning. It doesn't just look at the code; it looks at reachability specifically, can this vulnerable code actually be exploited from the internet?
- Old SAST: "Here is a vulnerability in library X." (Panic ensues).
- Modern SAST: "Here is a vulnerability in library X, BUT this code is only running on a private test server that has no internet access and no customer data. Priority: Low."
This allows the team to ignore the noise and focus on the 10 alerts that actually matter, the ones affecting our data.
Hunting the Keys to the Kingdom (SaaS API Keys)
One of the biggest threats in 2025 isn't a sophisticated hacker breaking in; it's a developer accidentally leaving the "front door key" under the mat.

We use the platform's Secret Scanning to hunt for SaaS API Keys and hardcoded credentials. Developers sometimes accidentally commit API keys directly into the code. If a hacker finds that key, they can move laterally through our systems.
The paltform scans our entire environment, from the code repository (GitHub) to the running container to find these secrets before they can be exploited. It doesn't just find the key; it validates it. It tells us: "This is an active Stripe API key with 'Admin' privileges..." We can revoke that key in minutes.
Data Security Posture Management (DSPM): Knowing Where the sensitive data Is
At ZenBusiness, protecting the data is equally important as protecting the server. We use DSPM capabilities to automatically classify data.
The platform scans our cloud buckets and databases to identify PII (Personally Identifiable Information) and other sensitive records. It then checks the permissions on those specific assets.
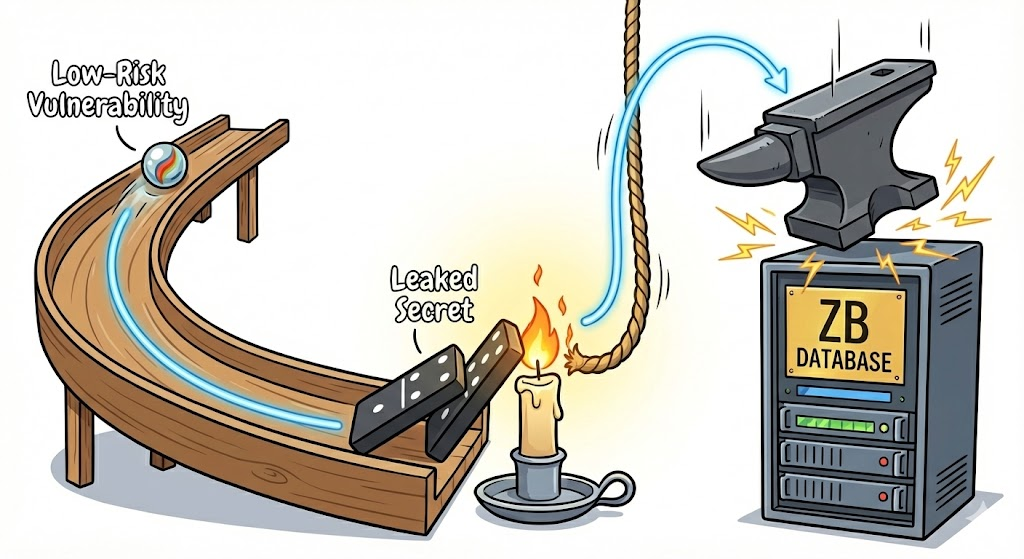
The "Toxic Combination" (Attack Path Analysis)
Collecting data is easy. Making sense of it is hard. We use our cloud security platform to filter the noise by looking for Toxic Combinations. This is when multiple low-level risks combine to create a critical Attack Path.
For example, a "Toxic Combination" in our environment might look like this:
- Public Exposure: A public-facing microservice has a known code vulnerability.
- Identity Risk: The VM runs with a default GCP Service Account holding broad
Editorpermissions. - Lateral Movement: That identity allows reading the unrelated
gs://customer-kyc-documentsbucket. - Critical Path: An attacker exploits the "low-risk" app to steal high-risk Customer data
The platform connects these dots on a Security Graph. It tells us: "Ignore the 500 minor patches; fix this ONE server immediately because it is a gateway to the ZB Database."
The Bottom Line
By using the platform to correlate SAST, API Keys, Cloud Infrastructure, and Sensitive Data, we have removed the friction between "being secure" and "being high-performance." We are scanning deeper, finding risks faster, and protecting your data better using a balanced strategy of agentless speed and forensic agent depth.